
In a world full of downloads, online accounts, and digital communication, security is more important than ever. This is exactly where SHA-256 comes into play. But what is it, how is it used in everyday life, and why does it make the digital world much safer? 🤔
🧩 What is SHA-256?
SHA-256 stands for Secure Hash Algorithm (256-bit). It is a cryptographic hash function that generates a fixed 256-bit hash value from any kind of input data (for example, a file or a text).
📌 Key properties:
- 🔁 Same input → same hash
- ✏️ Smallest change → completely different hash
- 🔒 One-way only (the original data cannot be reconstructed from the hash)
A SHA-256 hash can be compared to a digital fingerprint: unique and extremely sensitive to any changes.
🛠️ How is SHA-256 used in everyday life?
Even if it often goes unnoticed, SHA-256 is used everywhere:
🔐 Passwords
Passwords are usually not stored in plain text, but as hash values. This keeps them protected even in the event of a data breach 🔑
📦 Downloads & Files
SHA-256 makes it possible to verify whether:
- a file was downloaded completely
- a file was not modified or tampered with by malware
🌐 HTTPS & Certificates
SHA-256 is used in SSL/TLS encryption to ensure that websites are authentic and connections remain secure 🔏
⛓️ Blockchain & Modern Technologies
Blockchains and many other security mechanisms rely on SHA-256 to make manipulation practically impossible 🚀
🛡️ Why does SHA-256 make everything more secure?
✅ Integrity – any change is detected immediately
✅ Trust – files and data remain verifiable
✅ Proven & standardized – used worldwide
✅ Very high security – no practical attacks known today
👉 In short: SHA-256 is one of the core pillars of modern IT security.
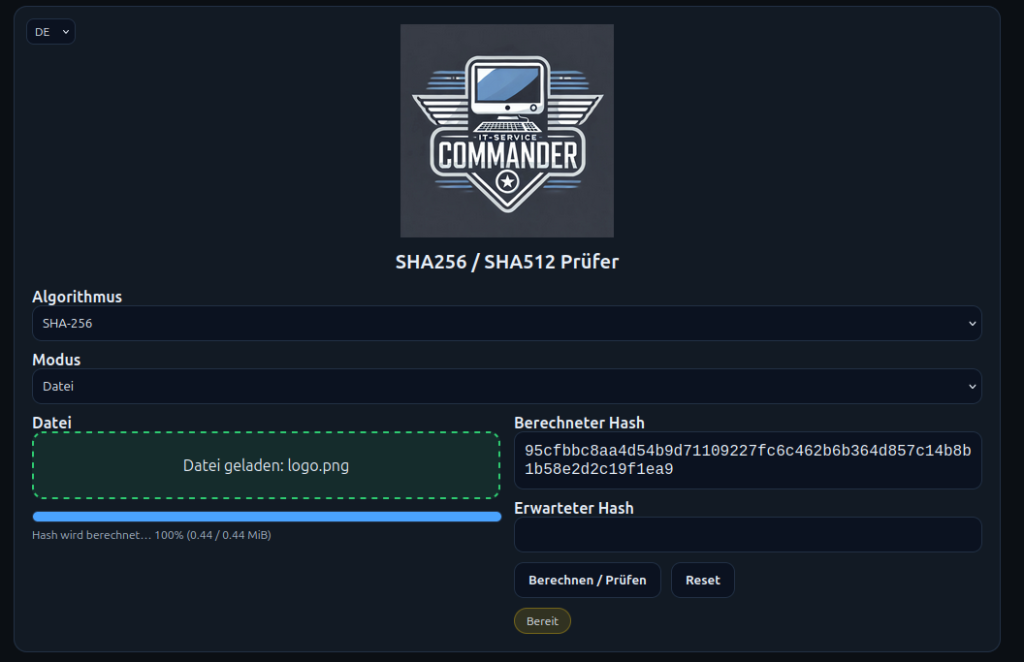
🧪 Verify SHA-256 & SHA-512 for free – useful tools
🪟 Windows
- 7-Zip (must be installed first)
- Right-click the file
- 7-Zip → CRC SHA → SHA-256
- SHA-512 can also be selected if needed
📌 Advantage: Easy to use via context menu, no command line required.
🐧 Linux
- sha256sum (available by default on most distributions):
sha256sum file.zip🌍 Online – free tool
For quick checks directly in the browser, my free tool is available:
https://sha.it-service-commander.de

🔧 Features:
- ✅ Calculation of SHA-256
- ✅ Calculation of SHA-512
- ✅ Free to use
- ✅ No installation required
- ✅ Ideal for checking files or text
📥 Downloads with verified security
One final important note:
All downloads available at
https://downloads.it-service-commander.de
🔐 are provided with SHA-256 checksums and can be verified. This makes it possible at any time to ensure that files are authentic, complete, and unchanged ✅
📌 Conclusion:
SHA-256 is invisible, but indispensable. It protects passwords, secures downloads, and builds trust in everyday digital life. Consistently verifying hash values significantly increases overall security 🔐💻
